Accelerating Our Economic Recovery: Zero Friction with Zero Trust
securityboulevard.com – 2021-09-02 18:00:00 – Source link
No event in our lifetimes has catalyzed such a profound paradigm shift as the mandate to shelter in place and the mass adoption of the hybrid workspace. Throughout the pandemic, small to medium-sized enterprise (SME) IT teams have been challenged to securely enable remote work. Even as organizations turn their attention toward economic recovery the hybrid workspace remains. This is driving many IT teams to adopt Zero Trust security, which focuses on managing and securing the identity of users and devices instead of an obsolete network perimeter.
According to the United Nation Conference on Trade and Development, “supporting small businesses is critical for COVID-19 recovery.” Therefore, the role that IT teams play in adapting to the challenges of the hybrid workspace cannot be understated. And make no mistake, managing hybrid workspaces is a challenge.
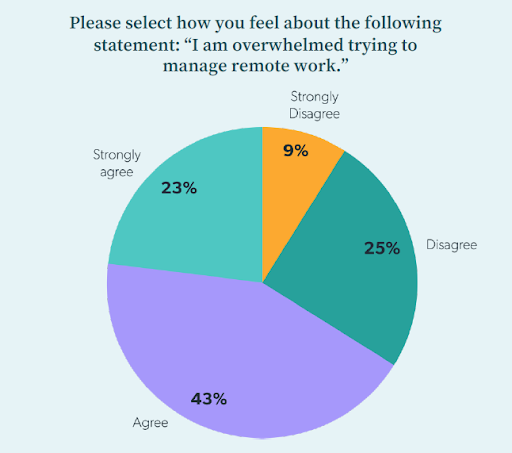
According to JumpCloud’s research, nearly two-thirds (66 percent) of SME IT professionals agree that they feel overwhelmed by remote work. Consequently, more than half plan to spend more on remote management technologies and security. For the remainder of 2021, the top priorities for SME IT leaders include securing remote work and making remote work easier. In fact, more than half of the SMEs we surveyed plan to have a Zero Trust security architecture implemented by the end of 2021 to help make this possible.
The Basics Of Zero Trust Security
Zero Trust security is a robust architecture that emerged during the past decade to address the rise of cloud services, mobile devices and remote workers, which have rendered the traditional network security model obsolete.
Organizations that have not implemented a Zero Trust security architecture may be relying on stop-gap solutions, such as virtual private networks (VPN) or virtual desktop infrastructure (VDI). However, these legacy solutions may suffer from performance issues and a poor user experience since they were developed with a more traditional network perimeter in mind – cloud services and remote employees can stress the limits of legacy solutions.
IT teams should still be concerned with protecting valuable data, but they need to reimagine security in terms of access. This is (Read more…)



