SafeBreach Coverage for US-CERT Alert (AA23-061A) – Royal Ransomware
securityboulevard.com – 2023-03-03 21:08:42 – Source link
On March 2nd, the Federal Bureau of Administration (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) released an advisory highlighting the malicious cyber activities carried out by threat actors leveraging the Royal ransomware to target U.S. and international critical infrastructure organizations. Details of this investigation (along with attacker TTPs and IOCs) were made available via US CERT Alert (AA23-061A) #StopRansomware: Royal Ransomware.
According to the advisory, threat actors have been targeting organizations since September 2022 using a Royal ransomware variant which uses its own custom-made file encryption program. The agencies believe that this file encryption program has evolved from earlier iterations of the ransomware that used “Zeon” as a loader. Based on the information available, post initial access, the threat actors disable AV software and exfiltrate data before deploying the ransomware and encrypting the systems. Ransom demands have ranged between $1 million to $11 million in Bitcoin. The threat actors have been observed NOT including ransom amounts and payment instructions as part of the initial ransom note. The ransom note requires the victims to communicate directly with the threat actors via a “.onion” URL – accessible via the Tor browser. Targeted victims include several critical infrastructure sectors including, Manufacturing, Communications, Healthcare and Public Healthcare (HPH), and Education.
Additional Technical Details
The investigation revealed that Royal ransomware uses a unique partial encryption approach that allows the threat actor to choose a specific percentage of data in a file to encrypt. This approach allows the actor to lower the encryption percentage for larger files, which helps evade detection. In addition to encrypting files, Royal actors also engage in double extortion tactics in which they threaten to publicly release the encrypted data if the victim does not pay the ransom. Additional technical details can be seen below –
- Initial Access – According to open-source reporting, the most common way threat actors have gained initial access to victim networks is via phishing when victims unknowingly installed malware that delivers Royal ransomware after receiving phishing emails containing malicious PDF documents and malvertising. Additionally, they have also been observed gaining initial access via RDP compromise, exploiting public facing applications, and using stolen VPN credentials.
- Command and Control Setup – Once Royal actors gain access to the network, they communicate with command and control (C2) infrastructure and download multiple tools including Chisel – a tunneling tool transported over HTTP and secured via SSH.
- Lateral Movement and Persistence – Royal actors often use RDP to move laterally across the network. Microsoft Sysinternals tool PsExec has also been used to aid lateral movement. FBI has observed Royal actors using remote monitoring and management (RMM) software, such as AnyDesk, LogMeIn, and Atera, for persistence in the victim’s network.]. In some instances, the actors moved laterally to the domain controller.
- Data Exfiltration – Royal actors exfiltrate data from victim networks by repurposing legitimate cyber pen testing tools, such as Cobalt Strike, and malware tools and derivatives, such as Ursnif/Gozi, for data aggregation and exfiltration. According to third-party reporting, Royal actors’ first hop in exfiltration and other operations is usually a U.S. IP address.
- Lateral Movement and Discovery – Post initial access, staged payloads with customized malware were used to perform recon activities, upload/ download of additional files and executables, and execute shell commands.
- Encryption – FBI has found numerous batch (.bat) files on impacted systems which are typically transferred as an encrypted 7zip file. Batch files create a new admin user, force a group policy update, set pertinent registry keys to auto-extract and execute the ransomware, monitor the encryption process, and delete files upon completion—including Application, System, and Security event logs.
Important Note for SafeBreach Customers – Coverage for AA23-061A
As soon as details and IOCs were made available, corresponding new attacks were immediately added to the SafeBreach Hacker’s Playbook on March 3rd. It is important to note that many of the attack TTPs used by these threat actors were already available in the SafeBreach playbook. SafeBreach customers already had an existing level of protection against these threat actors if their security controls were validated against these known TTPs.
on March 3rd. It is important to note that many of the attack TTPs used by these threat actors were already available in the SafeBreach playbook. SafeBreach customers already had an existing level of protection against these threat actors if their security controls were validated against these known TTPs.
Newly added playbook methods related to US-CERT Alert AA23-061A:
Chisel
- #8652 – Write Chisel hacktool to disk
- #8653 – Pre-execution phase of Chisel hacktool (Windows)
- #8654 – Transfer of Chisel hacktool over HTTP/S
- #8655 – Transfer of Chisel hacktool over HTTP/S
- #8656 – Email Chisel hacktool as a ZIP attachment
- #8657 – Email Chisel hacktool as a ZIP attachment
BatLoader
- #8658 – Write BatLoader downloader to disk
- #8659 – Transfer of BatLoader downloader over HTTP/S
- #8660 – Transfer of BatLoader downloader over HTTP/S
- #8661 – Email BatLoader downloader as a ZIP attachment
- #8662 – Email BatLoader downloader as a ZIP attachment
NirCmd
- #8663 – Write NirCmd hacktool to disk
- #8664 – Transfer of NirCmd hacktool over HTTP/S
- #8665 – Transfer of NirCmd hacktool over HTTP/S
- #8666 – Email NirCmd hacktool as a ZIP attachment
- #8667 – Email NirCmd hacktool as a ZIP attachment
Previously available playbook attacks related to US-CERT Alert AA23-061A:
IOC-based attacks:
Royal Ransomware
- #8203 – Pre-execution phase of Royal Ransomware
- #8204 – Write Royal Ransomware to disk
- #8205 – Transfer of Royal Ransomware over HTTP/S
- #8206 – Transfer of Royal Ransomware over HTTP/S
- #8207 – Email Royal Ransomware as a ZIP attachment
- #8208 – Email Royal Ransomware as a ZIP attachment
- #8290 – Pre-execution phase of Royal Ransomware (d429)
- #8291 – Write Royal Ransomware (d429) to disk
- #8292 – Transfer of Royal Ransomware (d429) over HTTP/S
- #8293 – Transfer of Royal Ransomware (d429) over HTTP/S
- #8294 – Email Royal Ransomware (d429) as a ZIP attachment
- #8295 – Email Royal Ransomware (d429) as a ZIP attachment
- #8296 – Pre-execution phase of Royal Ransomware (1926)
- #8297 – Write Royal Ransomware (1926) to disk
- #8298 – Transfer of Royal Ransomware (1926) over HTTP/S
- #8299 – Transfer of Royal Ransomware (1926) over HTTP/S
- #8300 – Email Royal Ransomware (1926) as a ZIP attachment
- #8301 – Email Royal Ransomware (1926) as a ZIP attachment
Chisel
- #5461 – Pre-execution phase of ar20-259a_chisel malware
- #5462 – Write ar20-259a_chisel malware to disk
- #5463 – Transfer of ar20-259a_chisel malware over HTTP/S
- #5464 – Transfer of ar20-259a_chisel malware over HTTP/S
- #5465 – Email ar20-259a_chisel malware as a ZIP attachment
- #5466 – Email ar20-259a_chisel malware as a ZIP attachment
- #5486 – Communication with ar20-259a_Chisel using HTTP
Behavioral attacks
Indicator Removal: Clear Windows Event Logs
- #7554 – Clear Windows Event Logs
Remote Desktop Protocol
- #192 – Brute force attack over RDP protocol
- #6473 – Agentless lateral movement via RDP
- #6909 – RDP Connection Between 2 Simulators
- #6910 – RDP Tunneling
Impair Defenses: Disable or Modify Tools
- #2267 – Add an exclusion to Windows Defender using PowerShell
- #2389 – Modify Firewall Rules using netsh.exe
- #5107 – Stop a service using net stop command
- #7144 – Unregister anti-malware scanning interface providers
- #7834 – Add Exclusions to Windows Defender
- #7835 – Disable Windows Defender from Registry
Delete shadow copy
- #6372 – Modify Volume Shadow Copy (VSS)
What You Should Do Now
Several attack methods related to this US-CERT Alert were already present in the SafeBreach Hacker’s Playbook . The playbook has now been updated with attacks that map to the new IOCs and TTPs identified in this US-CERT Alert. SafeBreach customers can now validate their security controls against these TTPs and IOCs in multiple ways.
. The playbook has now been updated with attacks that map to the new IOCs and TTPs identified in this US-CERT Alert. SafeBreach customers can now validate their security controls against these TTPs and IOCs in multiple ways.
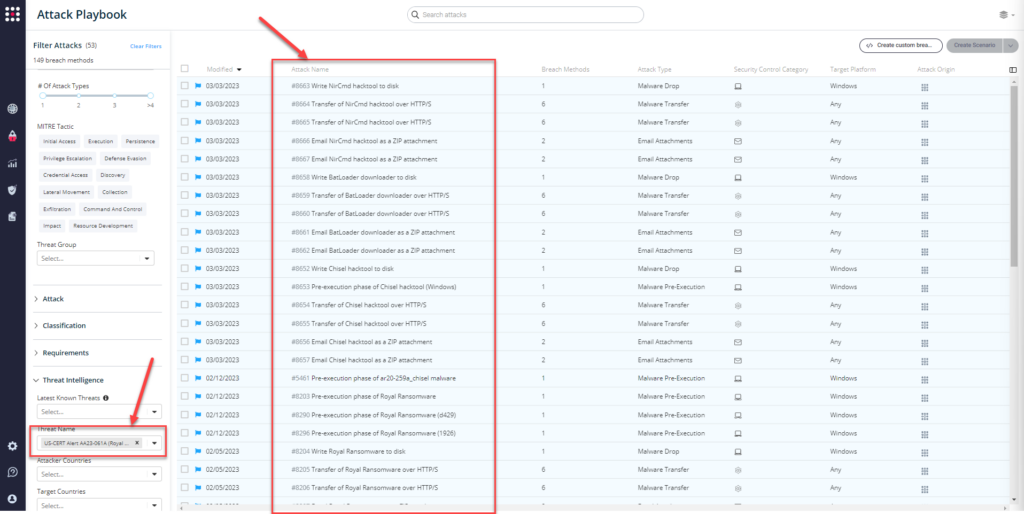
From the Attack Playbook, select and filter attacks related to AA23-061 (Royal Ransomware).
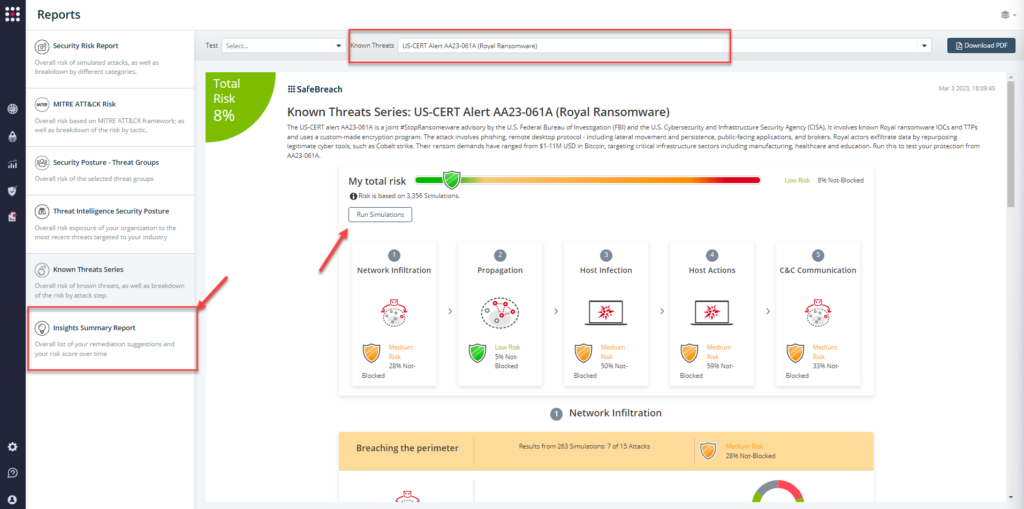
From the Known Attack Series report, select the AA23-061 (Royal Ransomware) report and select Run Simulations which will run all attack methods.
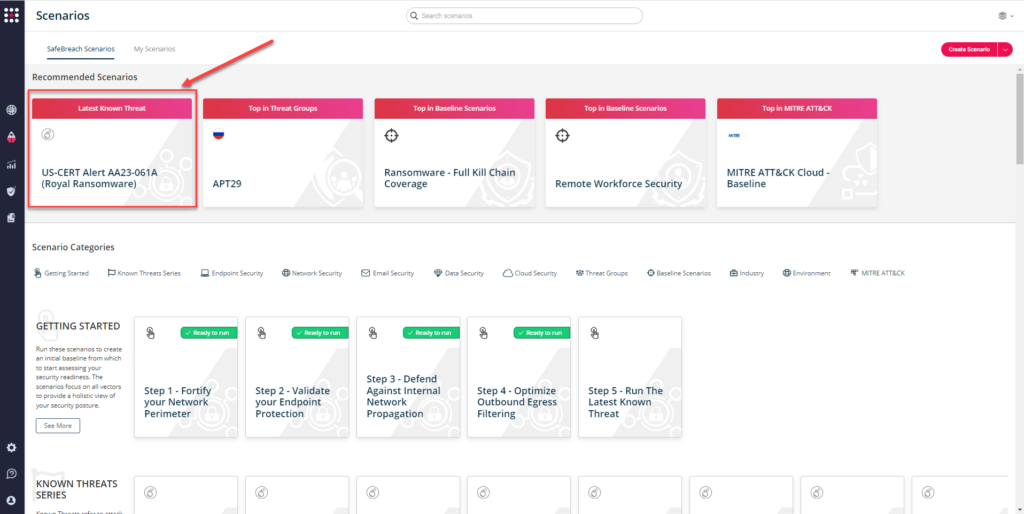
You can also go to the “SafeBreach Scenarios” page and choose the AA23-061 (Royal Ransomware) scenario from the list of available scenarios.
NOTE: The following actions have been recommended to mitigate any potential threats to their systems:
- Validate Security Controls – CISA and FBI recommend continually testing your security program, at scale, in a production environment to ensure optimal performance against the MITRE ATT&CK techniques identified in this advisory.
- Implement a recovery plan.
- Use longer passwords consisting of at least 8 characters and no more than 64 characters in length.
- Require multi-factor authentication.
- Keep all operating systems, software, and firmware up to date.
Additional Useful Resources
- Stopransomware.gov is a whole-of-government approach that gives one central location for ransomware resources and alerts.
- A resource to mitigate a ransomware attack: CISA-Multi-State Information Sharing and Analysis Center (MS-ISAC) Joint Ransomware Guide



