Uber Data Breach is Worst Case Scenario
securityboulevard.com – 2022-09-17 20:27:35 – Source link
Reading Time: 6 minutes
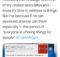
On Thursday, September 15, Uber, the ride-sharing giant, had a security incident after reports claimed a hacker had breached its internal network. Uber joins the ranks of other organizations, with 45% of businesses having experienced a cloud-based data breach over the past year. Uber’s current data breach is severe and wide-ranging, spreading access across their tech stack. This breach highlights the immediate need for credential-based lateral movement solutions that scan for credential detection outside of secret stores or vaults to reduce risk.

According to initial reports from the New York Times a bad actor compromised Uber because the company had weak security. Specifically, the attacker reportedly used social engineering to compromise an employee’s Slack account, persuading them to hand over a password that allowed them access to Uber’s internal systems, including Slack, AWS, and other areas of Uber’s tech stack.
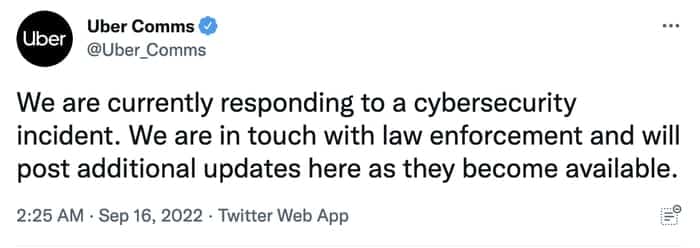
Once in Uber’s environment, the bad actor was able to move throughout the tech stack, gaining unimaginable access. While the attack started with a social engineering campaign on Uber employees, which yielded access to a VPN. It didn’t stop there. The bad actor gained access to the company’s internal network *.corp.uber.com.
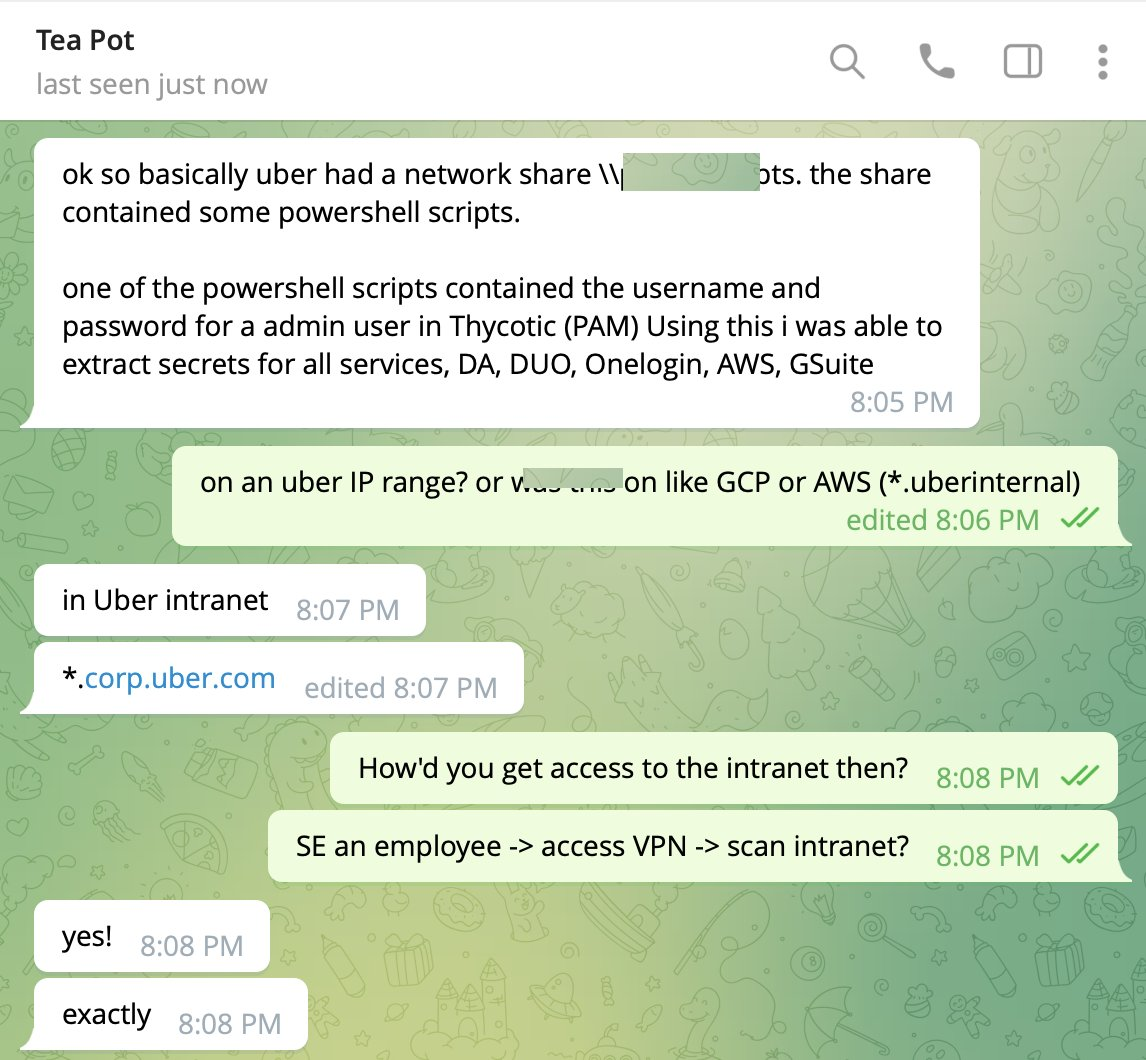
From Uber’s internal network, the attacker found PowerShell scripts, one of which contained credentials for an admin account from Uber’s Privileged Access Management (PAM) solution.
This PAM solution carries huge amounts of privilege, making it a valuable target. making it a single point of failure. The PAM controls access to multiple systems, and having admin access means the attacker can give themselves complete access or extract secrets to all connected systems. Critically, Uber’s platform was compromised through the exposure of its admin credentials. With that in mind, the attacker may have gained access to nearly all the internal systems of Uber. This is a worst-case scenario.
Using admin access, the attacker could log in and take over multiple services and internal tools used in Uber’s tech stack: Amazon Web Services, Google Cloud, Slack, SentinelOne, HackerOne, Uber’s internal employee dashboards, a few code repositories, and more.
In this case, no privilege escalation was needed, just a compromise of a single employee or endpoint, some simple reconnaissance, and admin credentials stored in a script on an internally open share. From that one point, the attacker won the crown jewels as they gained access to administrative privileged identities for Cloud, SaaS, or other critical systems at Uber.
The AWS instance controls the cloud infrastructure of Uber’s applications. Depending on configuration, privileges, and architecture, the attacker can potentially shut down services, abuse computing resources, access sensitive user data, delete or ransom data, change user access, and many more things.
The damage that can be done is no surprise to Sonrai Security. Sandy Bird, CTO and Co-founder of Sonrai Security, states, “In this case, the bad actors won the prize in very few steps. But even if they had only gotten low-level access to the AWS environment, we see why too many companies use poor IAM practices to allow lateral movement within the cloud environment. Approximately 10% of all cloud identities are configured as admin.”

Bird explains, “Access to any of those identities and their permissions could be detrimental.” Security teams will never patch every vulnerability, close every network path, stop every piece of malware, or prevent every credential compromise.
Companies need to understand their attack paths and the blast radius of credentials. They must scan file systems, automation scripts, cloud shells, and more. This is the only way to know where teams store, intentionally or unintentionally, credentials for automation and/or convenience. But this cannot be done manually or one time, and often, organizations do not understand their complete risk.
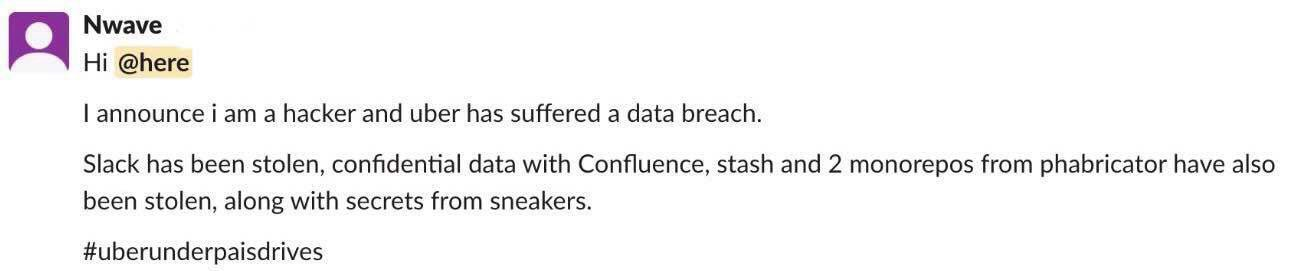
In the instance with Uber, it is reported that the company only found out about the compromise when it was alerting through Slack with Uber employees receiving a message that read, “I announce I am a hacker and Uber has suffered a data breach.” Lateral movement is a growing concern with cloud security. That is, once a piece of your cloud infrastructure is compromised, how far can an attacker reach? And as an organization, when will you be alerted to the breach?
“After working solely around the security of AWS, Azure, and GCP for the last 4 years, it is unfortunate we see the same data center patterns like this happening again in cloud.” Sandy Bird states, ”Most companies are still struggling with the basics of security, fighting to keep up with patches and compliance requirements when they need to be locking down the lateral movement from a single credential that gets compromised, allowing the attacker access to own the entire enterprise.”
Security extends to the whole cloud environment. This is why organizations must understand the context of their risk answering, who, what, and when someone has access to the environment. As Gartner points out, the challenge of protecting data lies not in the security of the cloud itself but in the policies and technologies used for securing it. In fact, Gartner predicts that through 2025, 99 percent of cloud security failures will be the customer’s fault.

What’s more, it predicts that through 2024, the majority of organizations will continue to struggle to appropriately measure cloud security risks. This is largely due to a widespread lack of visibility and control over data assets and identity security. It’s difficult to calculate risk if you don’t know where your information lives and who has access to it. That said, one of the most important things you can do when forming a cloud risk management strategy is to understand your blast radius and its potential impact on your company.
Uber isn’t the only organization making headlines this week with IHG hackers, a ‘vindictive’ couple, deleting the hotel chains data ‘for fun.’ Last Tuesday afternoon IHG told investors that it had been hacked. The attack was originally planned to be ransomware but became a wiper attack. A wiper attack is a form of cyber-attack that irreversibly destroys data, documents, and files. This incident further highlights how poor identity management strategies can lead to catastrophic damage.
During this week’s data breaches, we saw the adversaries who were able to escalate privileges stealthily. What if security teams could detect the compromise right after it happened? The truth is an organization can use the right tools.
Implementing controls around what has access to data is fundamental to any data security and compliance program. Although each unique cloud provider delivers services and APIs to manage identity and access to data for their stack, they are not standardized across all the stacks available (e.g., Amazon, Google, and Microsoft), do not address third-party data stores, and often require the use of low-level tools and APIs. Sonrai Dig resolves this problem through normalized views and control of cloud identity and data access.
Many workloads require access to tokens, passwords, certificates, API keys, and other secrets. To enable secure, auditable access to your secrets/keys and when they are being used, Sonrai Security offers Access Key Detection. Most data protection schemes can’t see inside key vaults and databases and only report on configuration and activity related to the object. Sonrai enables cloud teams to see the full picture of what’s truly happening inside vaults at every moment.
Direct, deep integration with the Secret Store itself means you always have a record of what identity changed or accessed a key and when they did it. What’s more, changes inside critical databases are tracked to give context-rich intel on the use of access to inform least access policies.
While organizations run an average of six different tools or features to secure their public cloud environments, 96% of decision-makers still report that their organizations faced security incidents in the last 12 months, which is why you’ll want to invest in a tool that provides you with total cloud security.
Sonrai Security provides your organization with a cloud security platform that can secure your cloud data by finding vulnerabilities, helping you repair them, and preventing future problems from occurring. Sonrai Security provides the data breach management tools necessary to help you manage and maintain a secure cloud going forward. Learn more about data security and how your organization can prevent similar data breaches. Contact Sonrai Security for more information on security solutions and services.
*** This is a Security Bloggers Network syndicated blog from Sonrai | Enterprise Cloud Security Platform authored by Eric Kedrosky. Read the original post at: https://sonraisecurity.com/blog/uber-data-breach-is-worst-case-scenario/